Ransomware is becoming a growing problem, posing a massive threat to all computer users – particularly businesses with many users and shared network drives. Rise of nations gold edition.
- Cryptolocker Virus For Testing For Coronavirus
- Cryptolocker Virus For Testing Sites
- Cryptolocker Virus For Testing Equipment
- Cryptolocker Virus For Testing For Covid 19
- Cryptolocker Virus For Testing Sites
The typical ransomware starts with a user being invited to “open” a document, but what they don’t realise that it is actually a program that silently starts encrypting every document the user has access to- even if they don’t have admin-rights on the computer. Once the files are encrypted the user offered the chance to decrypt the files for a fee. Rome 2 overhaul mods.
RanSim is a free tool for Windows that will simulate several ransom-ware style attacks and will let you know how vulnerable your computer is. Providing you the opportunity to test various anti-virus tools.
Download Cryptolocker Virus For Testing; Download Cryptolocker For Testing; Download Cryptolocker For Testing Reddit; For the last four years, ransomware has evolved into one of the biggest threats to cyber security that I’ve seen in a long time. Skype version 5. Names like CryptoLocker, CryptoWall, and CTBLocker keep average computer users and IT security. Dec 18, 2013 Several early versions of CryptoLocker, thought to be part of a beta testing phase, included code to connect to 184.164.136.134. This IP address is located in a PhoenixNAP datacenter in Arizona, but it was likely under the administrative control of Jolly Works Hosting.
It will ONLY simulate ransomware – it DOES NOT encrypt any files.

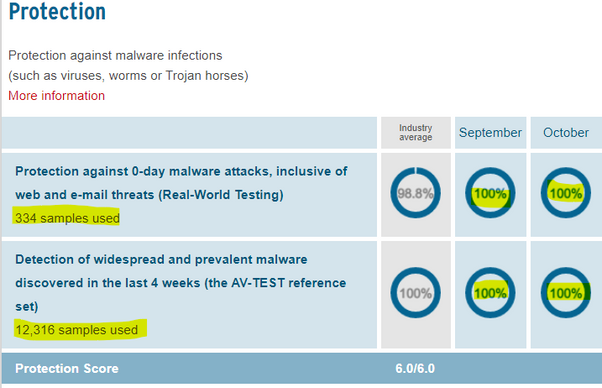
It tests vulnerability for:
- InsideCryptor – encrypts files using strong encryption and overwrites most of the content of the original files with the encrypted data.
- LockyVariant – simulates the behavior of a recent version of Locky ransomware.
- Mover – Encrypts files in a different folder using strong encryption and safely deletes the original files.
- Replacer – Replaces the content of the original files. A real ransomware would show a message that fools users into thinking they can recover them.
- Streamer – Encrypts files and writes data into a single file, using strong encryption, then deletes the original files.
- StrongCryptor – Encrypts files using strong encryption and safely deletes the original files.
- StrongCryptorFast – Encrypts files using strong encryption and deletes the original files.
- StrongCrytptorNet – Encrypts files using strong encryption and deletes the original files. It also simulates sending the encryption key to a server using an HTTP connection.
- ThorVariant – Simulates the behavior of a recent version of Thor ransomware.
- WeakCryptor – Encrypts files using weak encryption and deletes the original files.
DOWNLOAD: From the developer (requires personal information provided in a form) or from Major Geeks mirror.
Ransomware
Over the past few weeks, we've been seeing an increase in the number of spreading CryptoLocker malware. This new kind of ransomware has been hitting more users over the past few weeks. Compared to the month of September, the number of identified cases in October has almost tripled.CryptoLocker infections were found across different regions, including North America, Europe Middle East and the Asia Pacific. Almost two-thirds of the affected victims - 64% - were from the US. Other affected countries include the UK and Canada, with 11% and 6% of global victims, respectively.Previously, we discussed how these threats were arriving via email. CryptoLocker can be viewed as a refinement of a previously known type of threat called ransomware. Such 'improvements' are in line with our 2013 Security Predictions, where we mentioned that the focus of cybercriminals would be the refinement of existing tools, rather than the creation of entirely new threats.Cryptolocker Virus For Testing For Coronavirus


Cryptolocker Virus For Testing Sites
What can I do?There are different ways an individual or an organization can handle the CryptoLocker threat. Since this threat starts as spam carrying TROJ_UPATRE (a downloader), its success depends on the social engineering lures used in the message and how users would respond to it.Let us start off first with simple (but frequently ignored) safe computing practices to consider when opening emails and file attachments, in general:- Always check who the email sender is. If the email is supposedly coming from a bank, verify with your bank if the received message is legitimate. If from a personal contact, confirm if they sent the message. Do not rely solely on trust by virtue of relationship, as your friend or family member may be a victim of spammers as well.
- Double-check the content of the message. There are obvious factual errors or discrepancies that you can spot: a claim from a bank or a friend that they have received something from you? Try to go to your recently sent items to double-check their claim. Such spammed messages can also use other social engineering lures to persuade users to open the message.
- Refrain from clicking links in email. In general, clicking on links in email should be avoided. It is safer to visit any site mentioned in email directly. If you have to click on a link in email, make sure your browser uses web reputation to check the link, or use free services such as Trend Micro Site Safety Center.
- Always ensure your software is up-to-date. Currently there are no known CryptoLocker that exploits vulnerabilities to spread, but it can't be ruled out in the future. Regularly updating installed software provides another layer of security against many attacks, however.
- Backup important data. Unfortunately, there is no known tool to decrypt the files encrypted by CryptoLocker. One good safe computing practice is to ensure you have accurate back-ups of your files. The 3-2-1 principle should be in play: three copies, two different media, one separate location. Windows has a feature called Volume Shadow Copy that allows you to restore files to their previous state, and is enabled by default. Cloud storage services (such as SafeSync) can be a useful part of your backup strategy.
Cryptolocker Virus For Testing Equipment